“Uncontrolled access to data, with no audit trail of activity and no oversight, would be going too far. This applies to both commercial and government use of data about people”-John Poindexter (Former National Security Advisor of the United States)
Have you ever imagined how companies and government agencies guard their sensitive information free of unauthorised access or modification? What do they do to protect and assure accuracy of their data? The solution is an audit trail use. A data security and integrity feature is an audit trail. It is a document of actions or business transactions that are listed on a log file that can keep any modifications made on business data of a business or organisation. We are going to break down the kinds of audit trails, give an example of how they are applicable in different industries, and explain how they function.
What is an Audit Trail?
A thorough record that includes all events as well as actions inside a system, application, or network is known as an audit trail. A chronological record tracks the who, what and when and where of system activities. The system usually creates an audit trail automatically, but it can also be generated by a person. Regarding the audit trail, the Ministry of Corporate Affairs (MCA) introduced new rules that took effect on April 1, 2023. Firms must keep a record of each transaction they complete. This announcement was made by the MCA.
By summarising the audit trail concepts or the procedure, it can be defined as an audit trail that ensures transparency as well as accountability in business operations toward a record of a company, which comprises aspects such as financial transactions, operational activities, administrative responsibilities, etc. Also, the detailed record of the financial transaction will be helpful. The record has the capacity to identify financial irregularities in all of the transitions.
Why are Audit Trails Important?
Audit trails are important for the sake of data integrity and security. A complete history of all events, with actions taken within a system, is important for them in identifying plus investigating any unauthorised access, changes, or errors. For compliance assurance, audit trails are key because they enable companies to satisfy rules. These trails also help them to adhere to industry standards such as HIPAA, PCI-DSS, and SOX.
Besides the transactions, audit trail captures all the changes done to the books of accounts, whether addition, deletion or amendments, together with the date and the nature of change. Furthermore, this record gives details of the date, amount and nature of each transaction as in the case of a financial record. Moreover, it has details of each authorisation granted to transactions and changes, and also the name of the persons who authorised them. The audit trail also has the information about the acceptances and rejections of transactions, modifications, and the names of the individuals who accepted or rejected the same.
The timeline and date of access to the books of accounts are also recorded in the audit trail with the name of the person who accessed the books. Lastly, the audit trail contains all restoration and backup activities conducted with the accounting records. This path plays a significant role in ensuring the credibility of the financial records of a given company and acts as evidence in case there is an investigation.
Types of Audit Trails
There are four main audit trail types, each of which serves a specific purpose:
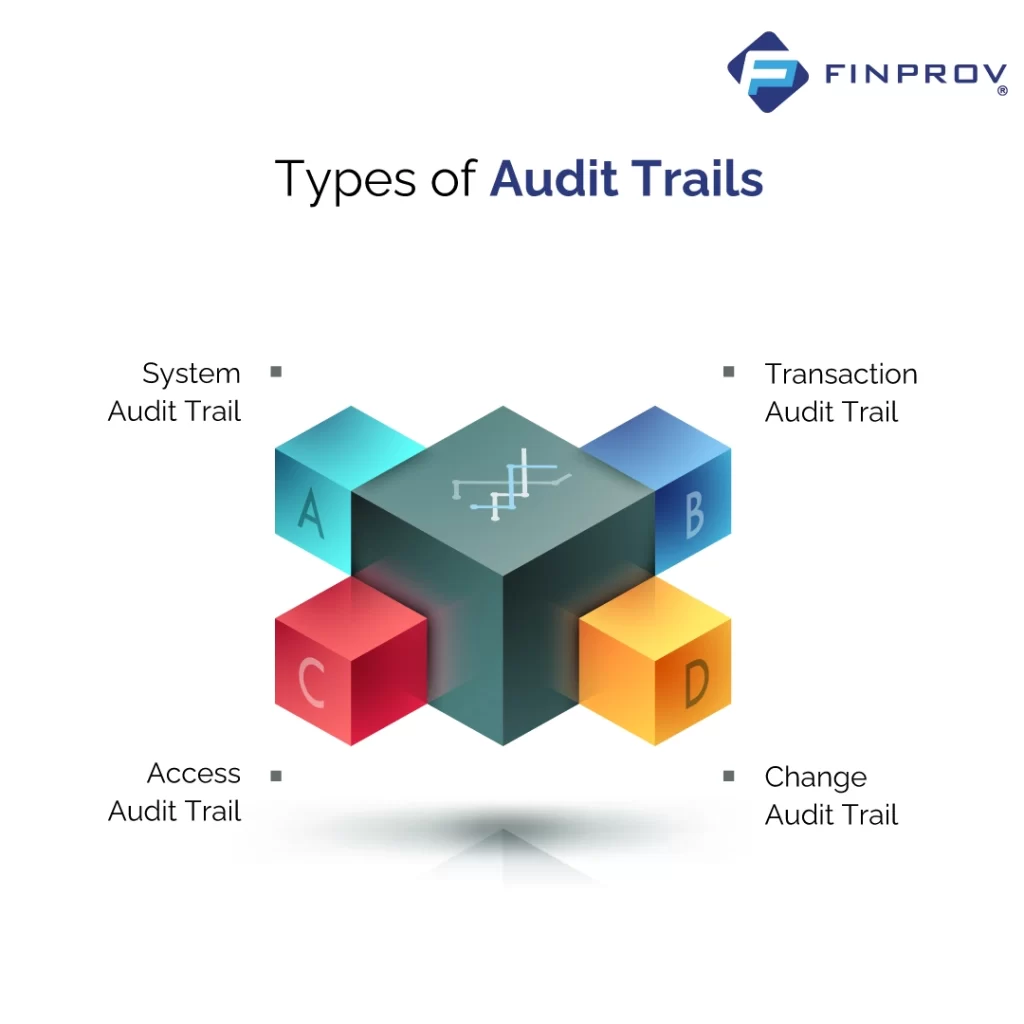
System Audit Trail: An audit trail on the systems captures the events at system level; these are system start-ups and shut downs, user log-ins and log outs, system configuration and security events. The audit trails of systems are important in the identification of attacks on systems, including unauthorised access, malware infection, and configuration changes.
Transaction Audit Trail: A transaction audit trail is an audit trail of events at transaction level, including data entries, updates, deletions and transfers. Data manipulation, fraud and theft are important issues and detection, along with investigation, requires transaction audit trails.
Access Audit Trail: An access audit trail is a log of all access-related events, e.g. access of files and folders, connections to the network, and remote access. One of the key requirements to prevent and trace the occurrence of illegal access and information fraud is an access audit.
Change Audit Trail: Change audit trail keeps the history of each change that occurred in system/application, like software updates, patches, and changes in configuration. Change audit trails are important in identifying and tracking down vulnerabilities, configuration flaws and errors in the system.
Examples of Audit Trails:
Audit trails are applicable in other businesses such as healthcare, finance, and government, among others, to maintain data security and integrity.
Banking and Finance: Audit tracks are normally applied in recording financial transactions such as deposits, withdrawals and transfers. This assists in avoiding fraud and meeting the regulations in place concerning finance.
Financial Industry: Forecasting. Financial organisations are subject to regulations such as PCI-DSS and SOX, which necessitate the creation and retention of audit trails. i.e. audit trails should be maintained in all financial transactions and access to sensitive information. The audit trails are necessary to identify and analyse fraud, unauthorised accesses and financial data errors.
Healthcare Industry: The audit trail is used in healthcare organisations, which concern HIPAA regulations that demand to establish audit trails and maintain it related to all the ePHI sent in an electronic form. Audit trails are necessary to help highlight and investigate the existence of any unauthorised access/change or mistakes involving patient data.
Government Agencies: The government agencies avail of audit trail so as to have transparency and accountability in their operations. Audit trail is vital to detect and investigate any unauthorised access, modification and error in sensitive information like national security information, tax records and criminal records.
E-commerce: Online purchases are tracked through audit trails which include order history, payment, and shipping information. This will help to guard against acts of fraud and adherence to the regulation of e-commerce.
How Audit Trails Work
To fully understand how the audit trails work, it’s important to revisit the concept of what is an audit trail. An audit trail is a chronological log that records every action, event, or transaction within a system.
Audit trails operate through the gathering of data concerning any event or transaction and storing that data in a secure log file. Reports or alerts are then prepared using predefined parameters based on the information in the log file. While audit trails can be created manually, they are typically automated through software for better accuracy, consistency, and real-time tracking.
Generating audit trail usually goes in the following steps:
- Determine what events or transactions have to be followed.
- Make the system or that application work to include audit trail records of such events.
- Keep the audit trial records at a safe place.
- Analyse the audit trail records by using software tools to detect abnormalities or some type of suspicious activity.
- Produce reports or alerts of the result of analysis.
The Benefits of Audit Trails
Audit trails provide several benefits, including:
Improved security and data integrity: Audit trails can be used to identify and avoid unauthorised access, alteration, amendment or destruction of sensitive data.
Regulations and policies: Audit trails are instrumental in ascertainment of compliance with industry regulations and internal policies as they give an avenue to monitor and perform an audit on regulations and policies.
Forensic capabilities for investigating security breaches or other incidents: Auditing logs maintain an entire record of system usage that can be utilised to research a security breach or other form of breach.
Enhanced process efficiency through identification of processes to be improved: Process improvements can be done based on the audit trails, hence making businesses more efficient in their operations.
Increased accountability for users and administrators: Audit trail offers a clear representation of what users and administrators have been doing, and this can make them more accountable, and fraud can also be eliminated.
With the growing importance of audit trails in ensuring compliance and transparency, careers in the accounting sector are evolving to require strong skills in data analysis, regulatory knowledge, and digital financial tools.
After all, audit trails form the security and compliance strategy in any organisation since they can prevent fraud, guarantee the enforcement of rules and policies, and improve the effectiveness of operations, making them trace and record the system activity. The new regulation says that an audit trail data record requires a business to have an eight-year data record relative to the year of financial assessment. Aspiring accountants, including in business organisations and people who desire to have a career in accounting sector, must know terms like audit trail, audit planning, audit articulation 1 and 2, Income Tax, GST and other aspects of finance so that they do not lag behind.
In today’s digital landscape, maintaining the integrity and security of data is essential. Knowing what is an audit trail helps us understand how organisations ensure transparency and accountability in their systems. By tracking who accessed data, what changes were made, and when, audit trails play a critical role in preventing misuse and building trust. As industries continue to rely heavily on digital information, audit trails remain a key component of responsible data management.
To upskill at each stage of your career journey, Finprov offers courses such as PGDIFA, PGBAT, CBAT, DIA, Income Tax, GST, etc., which are highly beneficial. Our team provides practical-oriented training based on real case studies. By obtaining valid certifications in various accounting courses and software such as SAP FICO, Tally Prime, Zoho Books, MS Excel, etc., aspirants can advance their accounting careers significantly.